QUICKLOOK: LightSpy Malware: CVE-2018-4233 and CVE-2018-4404 (macOS flavor)
Cross-Platform Threat: Leveraging CVE-2018-4233 and CVE-2018-4404 for Advanced Surveillance.
BLUF
Cybersecurity researchers have discovered that LightSpy spyware, previously thought to target only iOS users, also has an undocumented macOS variant. This new variant uses publicly available exploits (CVE-2018-4233 and CVE-2018-4404) to infect macOS systems, highlighting significant surveillance capabilities across multiple platforms. This indicates a sophisticated espionage campaign aimed at high-value targets, likely conducted by a well-resourced APT group.
Abstract
The discovery of a macOS variant of LightSpy spyware reveals significant cross-platform surveillance capabilities. By leveraging exploits CVE-2018-4233 and CVE-2018-4404, LightSpy demonstrates the ability to infect various operating systems, including macOS. This analysis explores the possible goals of this APT group, the selection of macOS and iOS targets, and compares LightSpy's surveillance approach to those used by groups like the NSO Group. The findings provide a comprehensive assessment of the threat posed by LightSpy.
Introduction
The emergence of the macOS variant of LightSpy spyware underscores the evolving nature of cyber threats and the increasing sophistication of state-sponsored surveillance tools. This report delves into the mechanisms of LightSpy, its exploitation of critical vulnerabilities, and the broader implications for cybersecurity. By examining historical events and potential scenarios, this analysis aims to provide a detailed understanding of the challenges posed by advanced spyware like LightSpy.
Analyst Comments
The emergence of a macOS variant of LightSpy spyware is a concerning development, as it expands the scope and reach of this sophisticated surveillance tool. Several key points are worth noting:
Cross-Platform Capabilities: By targeting both macOS and iOS devices, the group behind LightSpy demonstrates a commitment to developing a versatile surveillance toolkit. This allows them to cast a wider net and potentially compromise a larger pool of targets, regardless of their preferred operating system. LightSpy's cross-platform nature is reminiscent of other advanced spyware, such as FinSpy, which has been observed targeting Windows, macOS, Linux, Android, and iOS devices.
Exploit Usage: LightSpy's use of known vulnerabilities CVE-2018-4233 and CVE-2018-4404 highlights the importance of timely patching and updating. CVE-2018-4233, a Safari WebKit vulnerability, is exploited via malicious HTML pages to allow remote code execution. CVE-2018-4404, a macOS kernel vulnerability, enables privilege escalation. While these exploits are a few years old, their successful use suggests that many targeted devices may not have been properly patched, leaving them vulnerable to compromise. This is consistent with the tactics of other APT groups, which often rely on older exploits to target systems that may not be regularly updated.
Possible Goals and Targeting: The selection of macOS and iOS targets could indicate that the APT group is interested in surveilling specific individuals or organizations known to use these platforms. This might include journalists, activists, government officials, or business executives. These platforms are often chosen by high-profile individuals for their perceived security, making them attractive targets for espionage. The focus on macOS and iOS may also suggest a geopolitical motivation, targeting entities involved in sensitive international affairs, trade negotiations, or technological developments. Understanding the target profile can provide insights into the group's motivations and objectives.
Comparison to Other Surveillance Tools: LightSpy's capabilities appear to be on par with those of other sophisticated surveillance platforms, such as the NSO Group's Pegasus. Both aim to compromise high-value targets by exploiting vulnerabilities in iOS and Android devices (in the case of Pegasus) or macOS and iOS (for LightSpy). However, the specifics of LightSpy's functionality, stealth mechanisms, and C2 infrastructure may differ. The use of a plugin-based system allows LightSpy to adapt and expand its capabilities based on C2 commands, enabling audio capture, screen recording, file theft, and command execution. A more detailed technical analysis would be needed to fully assess how LightSpy compares to other spyware in terms of its efficacy and evasion capabilities.
Attribution Challenges: Attributing LightSpy to a specific APT group or nation-state actor may be difficult without further intelligence. However, the resources and skills required to develop and deploy such a sophisticated cross-platform surveillance tool suggest the involvement of a well-funded and organized group, potentially with state backing. In the past, APT groups linked to nation-states such as China, Russia, and North Korea have been known to develop and deploy advanced surveillance malware.
Key Findings:
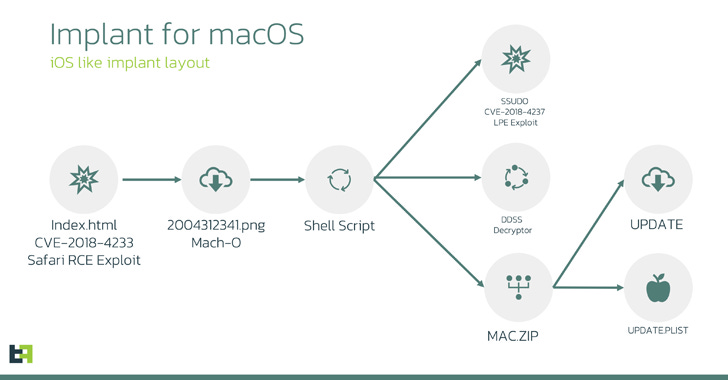
Initial Exploitation: The macOS variant begins its attack by exploiting CVE-2018-4233, a Safari WebKit flaw, via rogue HTML pages to trigger code execution. This leads to the delivery of a 64-bit MachO binary disguised as a PNG image file.
Payload Delivery: The binary extracts and launches a shell script that fetches additional payloads, including a privilege escalation exploit, an encryption/decryption utility, and a ZIP archive containing the main spyware components.
Persistence Mechanisms: The extracted files are assigned root privileges and set up to persist across system reboots, ensuring long-term access.
Command and Control (C2): The macOS variant uses a plugin-based system, allowing it to dynamically update its functionality via commands from the C2 server. It supports plugins for capturing audio, recording screen activity, harvesting files, and executing shell commands.
Detailed Exploit Stages:
Exploit Delivery:
CVE-2018-4233: Exploited via malicious HTML pages that trigger the WebKit vulnerability, allowing remote code execution (RCE).
CVE-2018-4404: Utilized for privilege escalation on macOS systems.
Initial Compromise:
The payload is delivered as a disguised PNG image file that contains a 64-bit MachO binary.
Script Execution:
The MachO binary extracts a shell script that executes to fetch additional payloads:
A privilege escalation exploit
An encryption/decryption utility
A ZIP archive
Payload Extraction:
The shell script extracts the contents of the ZIP archive and assigns root privileges to the files.
Persistence Setup:
The extracted files, including the "update" and "update.plist" files, are set to persist across system reboots.
C2 Communication:
The "update" file (macircloader) acts as a loader for the LightSpy Core component, allowing it to establish contact with a command-and-control (C2) server and retrieve additional commands and plugins.
Plugins and Capabilities:
Audio Capture: Records audio from the microphone.
Screen Recording: Captures screen activity.
File Harvesting: Steals files from the infected system.
Command Execution: Executes shell commands received from the C2 server.
Browser Data Extraction: Steals data from Safari, Google Chrome, and iCloud Keychain.
Proof of Concepts (PoCs)
CVE-2018-4233 GitHub PoC
Exploit Description: CVE-2018-4233 is a Safari WebKit vulnerability allowing remote code execution through crafted HTML content.
PoC Link: GitHub - CVE-2018-4233 PoC
Execution: Visit a malicious website with Safari to trigger the exploit.
CVE-2018-4404 GitHub PoC
Exploit Description: CVE-2018-4404 is an Apple macOS kernel vulnerability allowing privilege escalation.
PoC Link: GitHub - CVE-2018-4404 PoC
Execution: Execute the provided exploit script on a vulnerable macOS system.
Media Source
References: