QUICKLOOK: Navigating Quantum Frontiers: The Mozi Satellite and Security Implications
Assessing the Advances and Vulnerabilities in Quantum Key Distribution
Exploiting Quantum Key Distribution: Theoretical Vulnerabilities and Attack Vectors
Let’s look a recent article from South China Morning Post (SCMP). This Media source is Chinese state sponsored organization.
Event in Question:
Bottom Line Up Front (BLUF): Scientists from China and Russia have reported to have successfully tested an encrypted quantum communication system over a 2,300-mile distance, utilizing China's Mozi quantum satellite. This significant advancement in quantum technology promises a new era of virtually “unhackable” data transmission, reflecting the deepening high-tech collaboration between the two nations.
Analyst Comments: The successful test of the quantum communication link is a significant leap in technological advancement, promising a near-future of secure global communications immune to traditional hacking methods. This breakthrough reflects the strategic importance of quantum technologies in national security and underscores the escalating competition in the technological arena between major global powers. While the achievement marks a milestone in secure communications, it also signals the intensifying race for technological supremacy, where quantum advances hold key strategic value. The collaboration between China and Russia in this field denotes not only their mutual interest in secure communications but also a shared approach towards countering perceived threats from other technological powers.
FROM THE MEDIA: The recent quantum communication test conducted by China and Russia is a landmark in the ongoing development of quantum technologies, with the Mozi satellite playing a crucial role in the transmission of quantum keys over a vast distance. This test underscores the potential for quantum communication systems to provide unprecedented levels of data security, making it virtually impossible for third parties to intercept or decrypt the transmitted information. The collaborative effort is part of a broader international push towards realizing the practical benefits of quantum technologies, with implications for national security, economic communication, and beyond. While such advancements promise enhanced data security, they also raise questions about the balance of power in global communications and the future of cybersecurity in an increasingly quantum-enabled world.
READ THE STORY: Newsweek
Abstract:
Recent collaborative efforts between Russia and China have led to the testing of a quantum communication system, claimed to be highly secure and spanning an impressive distance of 2,300 miles between Moscow and Urumqi. While this development is touted as a significant milestone in quantum technology, suggesting a path towards virtually unhackable communication channels, it's essential to critically examine the extent of these claims. The role of the Mozi Satellite, launched by China in 2016, is central to this achievement, indicating progress in quantum key distribution (QKD). However, as with all emerging technologies, the assertions of unbreachable security warrant careful scrutiny, especially considering the theoretical and practical vulnerabilities inherent in current quantum communication systems.
Introduction:
As the digital landscape evolves, so does the need for more secure communication systems. Quantum Key Distribution (QKD) represents a paradigm shift in secure communications, promising levels of encryption that are theoretically impervious to traditional hacking methods. This quick-look explores the recent collaborative efforts between Russia and China in advancing quantum communication technologies. We delve into the technical nuances of the QKD process, including the generation and sharing of quantum keys using the Mozi Satellite and the theoretical vulnerabilities that could potentially be exploited by adversaries. Special emphasis is placed on understanding the implications of these advancements for international security and the ongoing efforts to mitigate potential exploits.
Mozi Satellite:
The Mozi Satellite, known as Micius (墨子), stands at the forefront of quantum communication, aiming to revolutionize secure data transfer across the globe. Launched in 2016, its primary mission is to create a space-based, ultra-secure quantum communication network utilizing quantum key distribution (QKD).
At the heart of Mozi's operation is the generation of entangled photon pairs through Spontaneous Parametric Down-Conversion (SPDC). This process is a fundamental aspect of quantum communication, particularly relevant to QKD. In SPDC, an incoming photon is split into a pair of entangled photons. These entangled pairs are then used to create secure communication channels between distant locations. Their entangled nature means that any interference or measurement of these photons will disturb their quantum state, thereby indicating a potential security breach.
A significant highlight of the Mozi Satellite's technology is the Acquisition Tracking and Pointing (ATP) system. The ATP system is crucial for the precise transmission and reception of the entangled photon pairs. It ensures the accurate tracking of the satellite's trajectory and the directed transmission of photons between Earth and the satellite. This precision is vital for the successful implementation of quantum communication, as it allows for the accurate calculation of the time difference of arrival (TDOA) of these photon pairs, essential for quantum positioning systems and other advanced quantum communication applications.
Quantum Review:
What is Quantum Computing?
Quantum computing is an area of computing focused on developing computer technology based on the principles of quantum theory, which explains the nature and behavior of energy and matter at the quantum (atomic and subatomic) level. Traditional computers use bits as the basic unit of data, which can be either a 0 or a 1. In contrast, quantum computers use quantum bits or qubits, which can be both 0 and 1 simultaneously thanks to a phenomenon known as superposition.
This ability to be in multiple states at once, coupled with the ability for qubits to be entangled (a quantum state of interdependence that allows the state of one qubit to depend on another), allows quantum computers to process a vast number of possibilities simultaneously. They hold the promise of massive leaps forward in processing power, leading to advances in various fields such as cryptography, materials science, pharmaceuticals, and complex system modeling.
What are Quantum Communications?
Quantum communication utilizes quantum mechanics to establish a secure method of transmitting information, such as cryptographic keys, between two parties. The core component of quantum communication is the quantum bit or "qubit," which, unlike a classical bit that represents a 0 or a 1, can represent both simultaneously due to the quantum phenomenon known as superposition. This dual state of qubits allows for more complex information processing and is the foundational element of quantum computing and quantum communication.
Quantum Key Distribution (QKD)
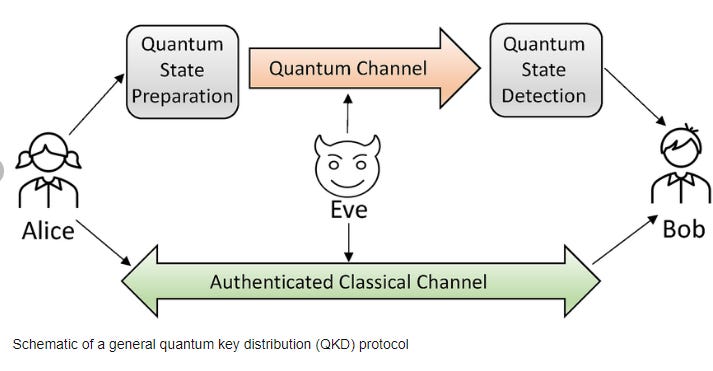
QKD is the most prominent application of quantum communication, allowing two parties, traditionally referred to as Alice and Bob, to generate a shared, secret cryptographic key. The security of QKD stems from the principles of quantum mechanics: any attempt to eavesdrop or measure the quantum states being communicated causes detectable disturbances. This sensitivity to eavesdropping is what potentially makes QKD secure against any type of interception.
The Role of Photons in QKD
In QKD systems, photons are typically used as the carriers of information due to their weak interaction with the environment and easy manipulation in terms of phase and polarization. These properties allow photons to embody the qubits effectively. The information is encoded in various ways, commonly through polarization states where different polarization (e.g., horizontal or vertical) represents different qubit states.
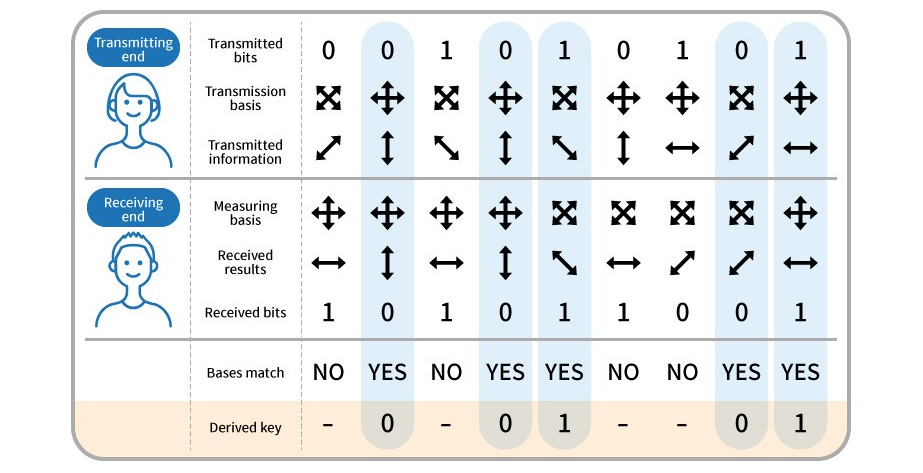
The BB84 Protocol
The BB84 protocol, proposed by Bennett and Brassard in 1984, is the first and one of the most well-known QKD protocols. Here is a simplified explanation of how it works:
Key and Control Bits Generation: Alice generates a random string of bits to form the basis of the key. She also generates a random string of bits as control bits to determine the encoding of the key bits.
Encoding of Bits: According to the value of the key bit and the control bit, Alice encodes each bit into a quantum state. These states are chosen from two conjugate bases (e.g., rectilinear {H, V} and diagonal {D, A}).
Transmission: Alice sends these qubits to Bob, who then randomly chooses a basis to measure each incoming qubit and notes down the result.
Basis Reconciliation: After the transmission, Alice and Bob disclose publicly which basis they used for each bit. They discard the bits where they used different bases (since the result would be random) and keep the rest.
Error Detection and Privacy Amplification: Alice and Bob perform error detection and privacy amplification procedures to detect any eavesdropping and to distill a shorter but secure key.
Security and Technological Implications:
To exploit the keys in the Quantum Key Distribution (QKD) system, particularly in the scenario where a secret key is distributed from a ground station in Zvenigorod to the Mozi satellite and then transmitted to China's Nanshan station, one would need to understand and exploit vulnerabilities in the QKD system.
Possible Attack Methods:
Photon Number Splitting (PNS) Attack:
Mechanism: QKD systems often use weak coherent pulses as approximations for single photons. Sometimes these pulses contain more than one photon. An eavesdropper, using a quantum non-demolition measurement, can ascertain the number of photons in a pulse without disturbing their quantum state. In the case of multi-photon pulses, the eavesdropper splits the pulse, keeping one photon and forwarding the others to the receiver. After the bases are disclosed in the public discussion phase of QKD, the eavesdropper can measure the intercepted photon in the correct base to gain partial information about the key.
Countermeasures: Modern QKD systems use decoy states and other techniques to detect and thwart PNS attacks. These methods make it extremely difficult for an attacker to carry out this type of attack without being detected.
Side-Channel Attacks:
Mechanism: These attacks exploit physical imperfections in the implementation of the QKD system. Every physical device has some level of imperfection or unintended emission, whether it's slight variations in photon detectors, timing devices, or other components of the system. An attacker might analyze these emissions or imperfections to gain information about the quantum states being transmitted or the functioning of the system.
Countermeasures: Rigorous shielding, filtering, and system characterization can help mitigate side-channel attacks. Additionally, continuous monitoring and testing of the physical devices used in QKD can detect potential vulnerabilities.
Quantum Hacking:
Mechanism: This involves sophisticated techniques like timing attacks or detector blinding. In timing attacks, by subtly manipulating the timing of photon arrivals, an attacker might influence the detectors' responses to reveal information about the key. Detector blinding involves sending intense light to the photon detectors to make them operate in a linear mode, wherein they are no longer sensitive to single photons, allowing the attacker to inject specific states that are detected as legitimate.
Countermeasures: Advanced calibration and monitoring of the timing and response patterns of detectors can detect anomalies indicative of such attacks. Newer detector technologies and protocols are also continually being developed to address these vulnerabilities.
Relay Attacks:
Mechanism: If an attacker can compromise or take control of a part of the communication channel, they might intercept or alter the quantum states being transmitted. This could involve physical takeover or hacking of the satellite or ground stations or interception of the photons during transmission.
Countermeasures: Ensuring secure, tamper-evident hardware and employing strict access controls can reduce the risk of physical takeover. Continuous monitoring of transmission patterns and immediate investigation of anomalies can also help detect and respond to any unusual activity.
Trojan Horse Attacks:
Mechanism: In a Trojan Horse attack, an attacker sends their own photons into the QKD system and then analyzes the back-reflected light to gain information about the system or the key. This requires the attacker to have some way of injecting light into the system and then collecting and analyzing the reflected light.
Countermeasures: QKD systems can be designed to detect and mitigate Trojan Horse attacks using optical isolators and monitoring incoming light levels. Careful system design can ensure that any injected light is either blocked or does not carry back useful information to the attacker.
Closing Thoughts:
As we stand on the edge of a transformative era with the advent of quantum communication technologies like the Mozi Satellite, it's essential to temper our optimism with a dose of reality about Quantum Key Distribution (QKD). While QKD promises a level of security that traditional encryption methods can't match, it's not an invulnerable fortress. Understanding the potential vulnerabilities and the evolving landscape of quantum hacking is crucial.
The pursuit of quantum communication, particularly QKD, is undoubtedly exciting. It uses the principles of quantum mechanics to create what many hope will be an unbreakable form of communication. However, as with all technologies, it's vulnerable to exploitation. The intricacies of implementing weak coherent pulse sources and photon detectors, the backbones of QKD systems, are not foolproof. They come with inherent vulnerabilities that can potentially be exploited by sophisticated quantum hacking strategies.
The arms race between encryption and hacking is as old as the field of cryptography itself, and it's naive to think that quantum communication will end this contest. Quantum hacking strategies, while still in their infancy compared to their classical counterparts, are evolving rapidly. Techniques like the Photon Number Splitting (PNS) Attack, Trojan Horse Attacks, and other side-channel attacks are reminders that even quantum communication isn't beyond the reach of potential adversaries.
The progress in QKD and quantum communications is encouraging, and innovations like the decoy-state method are making strides in enhancing security. Yet, the path to a truly secure quantum network is laden with challenges. Implementing efficient countermeasures, keeping pace with the potential for unknown attacks, and establishing the necessary infrastructure requires continuous effort and innovation.
The collaboration between nations on quantum technology projects signifies the recognition of quantum's strategic importance. However, it also underlines the global competition to achieve quantum supremacy, which is not just a matter of scientific prestige but of national security, economic advantage, and global influence.